Web Applications or Website Widgets
Over the past decade or so, the web has been embraced by millions of businesses as an inexpensive channel to communicate and exchange information with prospects and transactions with customers.
In particular, the web provides a way for marketers to get to know the people visiting their sites and start communicating with them. One way of doing this is asking web visitors to subscribe to newsletters, to submit an application form when requesting information on products or provide details to customize their browsing experience when next visiting a particular website.
The web is also an excellent sales channel for a myriad of organizations, large or small: with over 1 billion Internet users today (source: Computer Industry Almanac, 2006), US e-commerce spending accounted for $102.1 billion in 2006 (Source: comScore Networks, 2007).
Web applications defined
From a technical view-point, the web is a highly programmable environment that allows mass customization through the immediate deployment of a large and diverse range of applications, to millions of global users. Two important components of a modern website are flexible web browsers and web applications; both available to all and sundry at no expense.
How do web applications work?
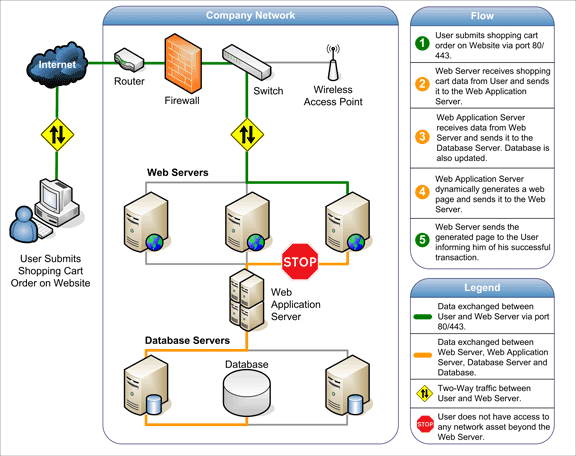
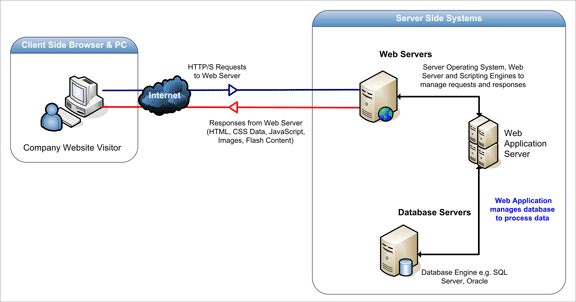
The figure below details the three-layered web application model. The first layer is normally a web browser or the user interface; the second layer is the dynamic content generation technology tool such as Java servlets (JSP) or Active Server Pages (ASP), and the third layer is the database containing content (e.g., news) and customer data (e.g., usernames and passwords, social security numbers and credit card details).
The figure below shows how the initial request is triggered by the user through the browser over the Internet to the web application server. The web application accesses the databases servers to perform the requested task updating and retrieving the information lying within the database. The web application then presents the information to the user through the browser.
Web Security Issues
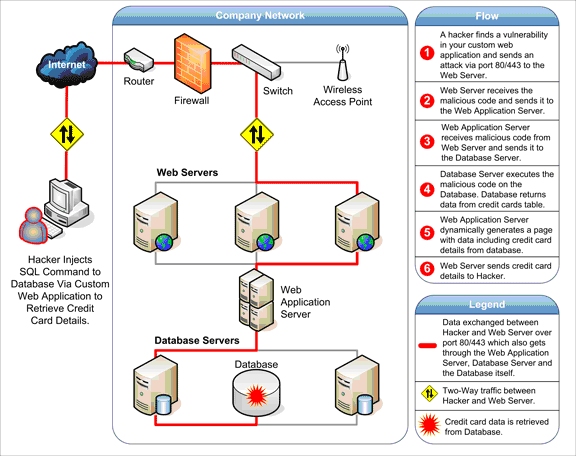
Despite their advantages, web applications do raise a number of security concerns stemming from improper coding. Serious weaknesses or vulnerabilities, allow hackers to gain direct and public access to databases in order to churn sensitive data. Many of these databases contain valuable information (e.g., personal and financial details) making them a frequent target of hackers. Although such acts of vandalism as defacing corporate websites are still commonplace, nowadays, hackers prefer gaining access to the sensitive data residing on the database server because of the immense pay-offs in selling the data.
In the framework described above, it is easy to see how a hacker can quickly access the data residing on the database through a dose of creativity and, with luck, negligence or human error, leading to vulnerabilities in the web applications.
As stated, websites depend on databases to deliver the required information to visitors. If web applications are not secure, i.e., vulnerable to, at least one of the various forms of hacking techniques, then your entire database of sensitive information is at serious risk.
Some hackers, for example, may maliciously inject code within vulnerable web applications to trick users and redirect them towards phishing sites. This technique is called Cross-Site Scripting and may be used even though the web servers and database engine contain no vulnerability themselves.
Recent research shows that 75% of cyber attacks are done at web application level.
- Websites and related web applications must be available 24 hours a day, 7 days a week, to provide the required service to customers, employees, suppliers and other stakeholders.
- Firewalls and SSL provide no protection against web application hacking, simply because access to the website has to be made public – All modern database systems (e.g. Microsoft SQL Server, Oracle and MySQL) may be accessed through specific ports (e.g., port 80 and 443) and anyone can attempt direct connections to the databases effectively bypassing the security mechanisms used by the operating system. These ports remain open to allow communication with legitimate traffic and therefore constitute a major vulnerability.
- Web applications often have direct access to backend data such as customer databases and, hence, control valuable data and are much more difficult to secure. Those that do not have access will have some form of script that allows data capture and transmission. If a hacker becomes aware of weaknesses in such a script, he may easily reroute unwitting traffic to another location and illegitimately hive off personal details.
- Most web applications are custom-made and, therefore, involve a lesser degree of testing than off-the-shelf software. Consequently, custom applications are more susceptible to attack
Web applications, therefore, are a gateway to databases especially custom applications which are not developed with security best practices and which do not undergo regular security audits. In general, you need to answer the question: “Which parts of a website we thought are secure are open to hack attacks?” and “what data can we throw at an application to cause it to perform something it shouldn’t do?”.
This is the work of a web vulnerability scanner.
Download instapro 2025 APK and enjoy advanced Instagram features like media downloads, enhanced privacy, and an ad-free experience. Get the latest version now!
ReplyDeleteVisit Techlancers Middle East a leading and top web development company in dubai providing top expertise in website domain.
ReplyDeleteGreat blog and you should visit CMOLDS a leading and authentic web app development usa service provider.
ReplyDelete